Introduction:
Penetration testing, also known to many as “pen testing,” is when a simulated cyberattack is conducted against a computer system, network, or web application to assess the exploitation of vulnerabilities. The purpose of penetration testing is to check for vulnerability exploitation in the system so that appropriate steps to prevent such attacks are taken in advance by malicious hackers. This will let organizations know if any blind spots or loopholes might exist within their security defenses and give further actionable insight to improve overall security.
I hope this article will help you with pen-testing methodologies, significance, process, and various types.
Why Penetration Testing Is Important:
- It helps detect flaws and a real-world attack on your confidential information, business systems, financial assets, and employees.
- It can detect breaches when occurring whether they are internal or external.
- Pen-testing though has some automated features but it still relies on skilful experienced analysts who can view networks in the same way as cyber-criminals do.
- Individual security tools seldom attract cybercriminals. Rather than this, they try to find out the loopholes from the poor integration among tools. Well, This is a comprehensive pen test.
- It is completely impartial or never enough ever. There remain instances where a new pair of eyes brings out weaknesses that had been overlooked.
Types of Penetration Testing
- Web Application
- Network
- Mobile Application
- Cloud
Web Application:
Web Application Penetration Testing is conducted to offer an assessment of the web application for any possible exploitable weaknesses. This type of testing concentrates on verifying the authentication mechanisms, input validation, data, and configuration security management against threats such as SQL injection, cross-site scripting (XSS) and insecure data storage.
Network:
Network Penetration Testing seeks to evaluate the level of security that network infrastructures have by looking for and exploiting the vulnerabilities in the network devices and services. Key areas include network mapping, vulnerability scanning, attempted exploitation, and configuration issues with potential for risk due to operating systems, network protocols, and settings of devices.
Mobile Application:
Mobile Application Penetration Testing is the assessment of mobile applications on the mobile operating platforms of iOS and Android for any security defects or vulnerabilities. The testing includes areas like source code review, protection of sensitive information stored within the app, information transfer within the network, and the permissions of the application to make sure that such information will not be leaked out and the app will spout no malicious behavior.
Cloud:
Cloud Penetration Testing emphasizes securing cloud environments by identifying and addressing vulnerabilities in cloud configurations, access controls, and data protection. This type of testing which involves cloud service configurations, IAM policies, data encryption, and integration security makes sure that cloud-hosted resources are enough safeguarded against potential threats.
Basic Methodologies:
Black Box Testing
- Black box testing is when it is conducted without any prior knowledge of the internal workings. A tester will provide an input and then observe what output the system under test received. It is possible to determine how a system responds, the system’s response time to expected and unexpected user actions, issues with usability, and reliability issues.

White Box Testing
- White box testing techniques are meant to analyze the internal structures, using data structures, internal design, code structure, and working of software rather than only functionality, as in black box testing. It is also called glass box testing, clear box testing, or structural testing. White Box Testing is also referred to as transparent testing or open box testing.
Grey Box Testing
- Grey-box testing, also known as gray-box testing, is a software debugging technique aimed at finding vulnerabilities. In doing so, the tester will have to acquire some knowledge about how the component he is testing functions. This is different from black box testing, where the tester doesn’t know anything, and white box testing, where the tester knows everything.
Important Tools For Penetration Testing:
- Nmap: This is a very powerful network scanning tool for host discovery and services on a computer network.
- Wireshark: This is a protocol analyzer of networks for recording and displaying data traveling over the network.
- Burp Suite: A well-known set of Security Testing tools for Web Applications that bundles together various tools for mapping and analyzing.
- Metasploit: A penetration testing framework that provides information about security vulnerabilities and assists in the development and execution of exploit code.
- Nikto: The tool scans web servers for dangerous files, outdated server software, and other common security problems.
- John the Ripper: It is a fast password cracker.
- Hydra: It performs brute-forcing to get login credentials over many protocols and services.
- OWASP ZAP: An open-source Web application security scanner for vulnerabilities in Web Applications.
- SQLmap: Automatic detection and exploitation of SQL injection vulnerabilities in Web Applications.
- Dirb/Dirbuster: Tools for brute forcing directories and file names on Web Servers to find hidden resources.
Steps Of Penetration Testing:
So, Here are some phases of penetration testing:
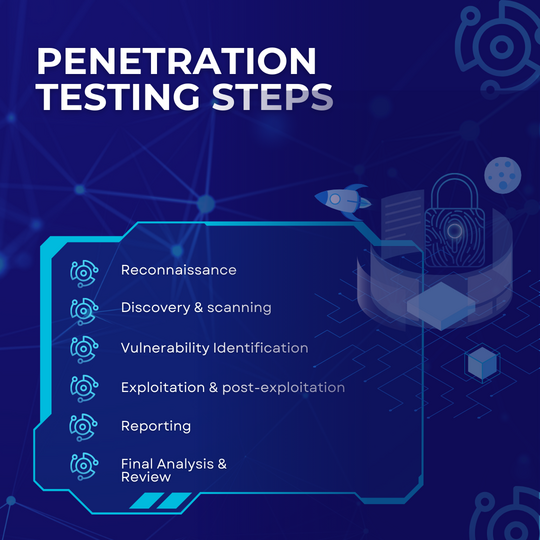
- Reconnaissance (Information Gathering):
This is the first step, whereby one tries to obtain as much information as possible about the chosen target. This process involves gathering information about domain names, IP addresses, network-related information, and all public records. The objective is to pull in information regarding target infrastructure, technologies, and possible weak entry points.
During this phase, you actively probe the target using the information gathered. This might include network scanning, looking for open ports, and determination of what services are running on those ports. All these provide a mapping of the target environment and identification of any possible vulnerabilities.
- Discovery and Scanning:
Later, you conduct deep scans to detect live hosts, the number of open ports, available services, and running operating systems. For vulnerability detection inside the target’s systems, you may use Nmap or Nessus; it helps you to identify specific vulnerabilities that an exploit could be associated with.
- Vulnerability Identification:
This phase entails the processing of the collected data in the scanning phase to acquire certain vulnerabilities in the target system. You estimate the degree of the vulnerabilities and prioritize them by possible impact. In this part, you can use, for example, Metasploit or Burp Suite. This phase involves exploiting the identified vulnerabilities to access unauthorized systems, data, or networks. Within this, you will see how deep you can go and what kind of damage or access you could do being an attacker.
- Exploitation:
Exploiting Vulnerabilities – SQL injection, cross-site scripting (XSS), or any other. Gaining Access: Using exploit kits to gain access to the target system (for instance through either compromised credentials or even privilege escalation).
- Post-Exploitation:
Maintaining Access As soon as the accessibility is successful, check if it can be continued in any manner (e.g., by providing a backdoor or pivoting on another system). Data Exfiltration: Determine how sensitive data may be taken away (e.g., copying database files, or capturing traffic.
- Reporting:
Document Findings – Give a comprehensive breakdown of discovered gaps how they were utilized and estimated consequences thereof. Recommend Remediation: Propose possible ways of fixing these vulnerabilities.
- Final Analysis and Review:
Following exploitation, you analyze the results of the testing and documenting, that is, what vulnerabilities were exploited, what access was gained, and what data was compromised. That is helping to understand the security posture of the target at the same time as being prepared with the groundwork for reporting.
In the final stage, you draw up a detailed report of the results from your vulnerability search, successful exploits, and remediation recommendations. It shares the report with the stakeholders to improve security defenses and fix the vulnerabilities identified during the test.
Difference between Automated and Manual Testing.
- Automated Testing:
In automated real-world testing, scripts and testers’ tools are employed to perform known test cases at a faster pace. This approach has proved to be quite effective where simple tasks have to be executed repeatedly, for example very often end-users wish to have rapid interaction testing and latency testing done. Large-scale implementations can be well carried out using this since it easily cuts across complicated and previously solved problems with a grip on preventing their reappearing.
- Manual Testing:
Human testers are the individuals performing test cases and evaluating the software behavior in manual testing. This method is useful in this situation because it grooms an agile development environment where complex bugs can be found and end usage of the software is tested. Manual testing is convenient when some actions may not altogether be automated like user acceptance testing of new functionalities or rare occurrences. Even though it is less efficient and more variable than automation, many observations that would be lost in automated testing will be captured after testing manually.
Resource from where you can learn penetration testing:
- Books:
- The Web Application Hacker’s Handbook
- Metasploit: The Penetration Tester’s Guide
- Hacking: The Art of Exploitation
- Online Courses:
- TryHackMe and Hack The Box for hands-on labs
- OSCP for deep diving and Certification
- Udemy for Various Penetration Testing courses
- PNPT
- YouTube Channels:
- Hackersploit, The Cyber Mentor, IppSec for Tutorials/Walkthroughs, STÖK (@STOKfredrik)
- Blogs and Websites:
- OWASP for security resources
- PortSwigger Web Security Academy for free labs
- SecurityTube for video tutorials
- Hackerone writeups
- Hacktricks.xyz
- Laburity writeups
- Practice Labs:
- VulnHub for downloadable virtual machines
- CTF platforms like CTFtime and PicoCTF
- Communities:
- Reddit, NetSec Focus Slack for discussion, and Knowledge sharing. Mastodon Communities
Expand Your Knowledge: Recommended Reads from Our Blog:
Conclusion:
This makes penetration testing one of the most important practices within the cybersecurity framework. In this process, very important information is gathered regarding vulnerabilities, to take countermeasures to help protect organizations from potential cyber threats. It improves the security posture of any organization by applying the right methodologies.




