Summary:
Greetings, today we will be sharing an XSS WAF bypass vulnerability that was identified by one of your Application Penetration Testers while working for a client’s audit. Due to the privacy concerns let’s call the target redacted.com.
What is the file Upload Vulnerability?
A file upload vulnerability is a type of security vulnerability that occurs when a web application allows users to upload files (such as images, documents, or scripts) to the server without proper validation or security controls in place. This vulnerability can be exploited by attackers to upload malicious files onto the server, which can then be executed or accessed by other users, leading to various security risks such as:
- Code execution: Attackers may upload scripts or executable files that can be executed by the server, leading to unauthorized code execution and potential compromise of the server.
- Data leakage: Attackers can upload sensitive files containing confidential information, such as user credentials, financial data, or proprietary information, leading to data leakage.
- Server compromise: By exploiting file upload vulnerabilities, attackers can gain unauthorized access to the server, allowing them to tamper with files, escalate privileges, or launch further attacks against other systems or users.
- Denial of Service (DoS): Attackers may upload large files or cause the server to run out of resources by uploading files in rapid succession, leading to denial of service for legitimate users.
Discovery
During the penetration testing engagement, we discovered a feature that lets us upload only the legitimate and valid files. We tried to upload a bad PHP file, but it didn’t work. The backend was validating that only valid images or document files should be uploaded.

Unrestricted File Upload Bypass
During engagement several file upload bypass techniques were tried out .After researching various file upload bypass techniques, only one proved effective and resulted in bypassing the file upload functionality. We simply utilized the use of double extension to bypass the file upload and the file name looked like this “test.html.png“. Sweet !
Following this success, We attempted to inject a cross-site scripting payload, “><script>alert(1)</script>”, anticipating an alert within the AWS S3 bucket. However, our request was obstructed by a Web Application Firewall (WAF). Subsequently, I modified the payload to “><img src=1 onmouseleave=alert()>”, but it was not successful.

Cloudflare Bypass
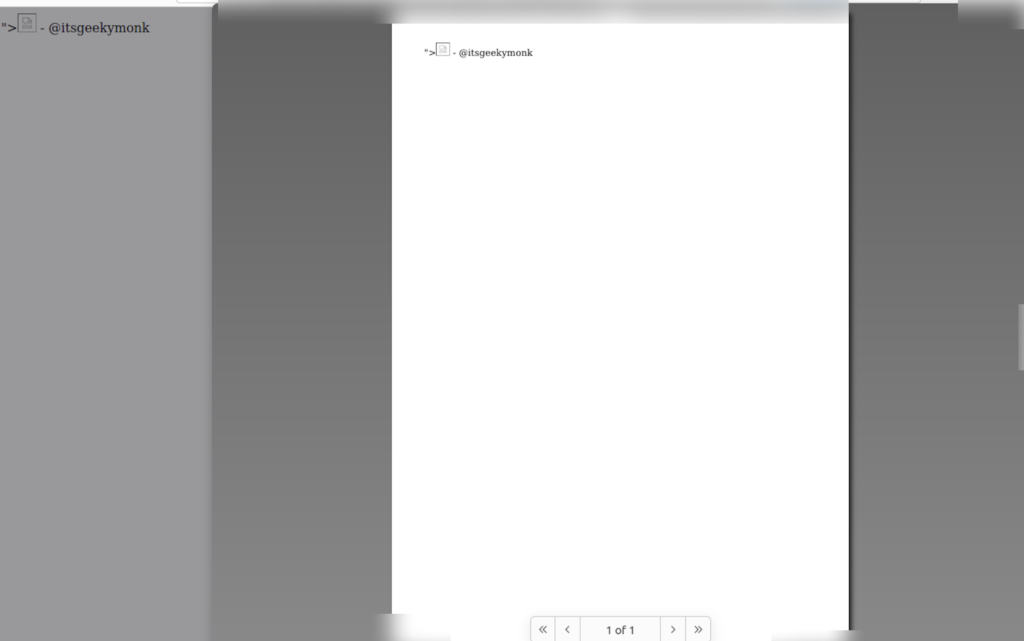
Executing a cross-site scripting attack without bypassing Cloudflare proved unattainable. Attempts to substitute ‘alert()’ with alternatives like ‘prompt()’ were unsuccessful. Only the ‘print()’ function yielded results. Surprisingly, modifying the payload to “><img src=1 onmouseleave=print()> – @itsgeekymonk proved effective, executing within targets’ AWS S3 bucket seamlessly.

When I opened the URL into the browser, the print() function got executed.
Conclusion
In short, we found out that redacted.com has some security measures that stopped us from uploading harmful files or executing certain commands and hurdled in executing the Javascript. We tried different tricks to get past these measures, like changing file extensions and implementing certain bypasses. Eventually, we found a way to make things work like changing the file name to test.html.png and the payload was modified from alert() to print() to bypass the firewall.