APIs (Application Programming Interfaces) are essential tools that allow different software systems to communicate with each other. A practical example is the Google Maps API. Imagine you’re using a travel booking website to find hotels in a specific area. When you see a map displaying hotel locations, that’s the Google Maps API at work. It enables the website to integrate Google’s mapping services, providing you with interactive maps, directions, and location data. This smooth integration improves your experience by blending the website’s functionality with Google’s powerful mapping tools. But this widespread use also comes with important responsibilities and potential cybersecurity risks. The increasing reliance on APIs has made them prime targets for cyberattacks, highlighting the importance of implementing strong security measures.
This guide is made for both technical professionals and curious non-technical readers who want to understand API security and learn the basics of penetration testing. By the end, you’ll grasp the importance of securing APIs and know how to identify vulnerabilities before malicious actors exploit them.
What is API Penetration Testing?
API penetration testing is all about simulating attacks on an API to find security vulnerabilities before real hackers do. Think of it like testing a lock on your door, not just to see if it locks, but to check if someone could pick it, force it open, or sneak in another way. The goal is to spot the weak spots and fix them before trouble comes knocking.
Imagine your API is a house. A security tester would check if the front door locks properly, if the windows can be forced open, or if there’s a hidden key under the doormat. In other words, they want to make sure only the right people (or systems) can get in.
API pentesting focuses on objectives such as:
- Identifying vulnerabilities that could expose sensitive data.
- Make sure authentication and authorization are solid.
- Testing the API’s security against common cybersecurity vulnerabilities like SQL injection or Cross-Site Scripting (XSS).
Why API Security Matters
APIs are a prime target for cybersecurity risks because they power so many everyday services, from mobile banking apps to online shopping and healthcare systems. Some real life case studies:
In 2018, Strava, a popular fitness tracking app, faced a significant security breach due to improper access control in its API. The app allowed users to share their workout routes publicly. When these routes were put together, they accidentally showed the locations of military bases and the movement patterns of soldiers, which shouldn’t have been exposed. You can read more about the breach here.
Similarly, Laburity identified an improper access control vulnerability that allowed a user to access sensitive administrator data, including personal information and unrestricted access to the admin dashboard. This exposure of private records posed a serious security risk, as it could lead to unauthorized access to critical administrative functions. You can read more about this real-case scenario here.
In 2018, Facebook’s API exposed millions of users’ private data. The breach was caused by flaws in its API’s authentication and authorization methods. You can read more about the breach here.
According to an 2018 Akamai traffic review, 83% of web traffic now flows through APIs, making them a focal point for attackers.
Insecure APIs can result in:
- Data leaks
- Financial losses
- Reputational damage
- Regulatory non-compliance
The increasing reliance on APIs across industries like fintech, healthcare, and e-commerce makes their security a non-negotiable priority. Organizations must ensure their APIs are secured against cybersecurity vulnerability to protect sensitive user data and maintain trust.
Types of API Penetration Testing
Pentesters use different approaches based on their knowledge of the API. Here’s a quick breakdown:
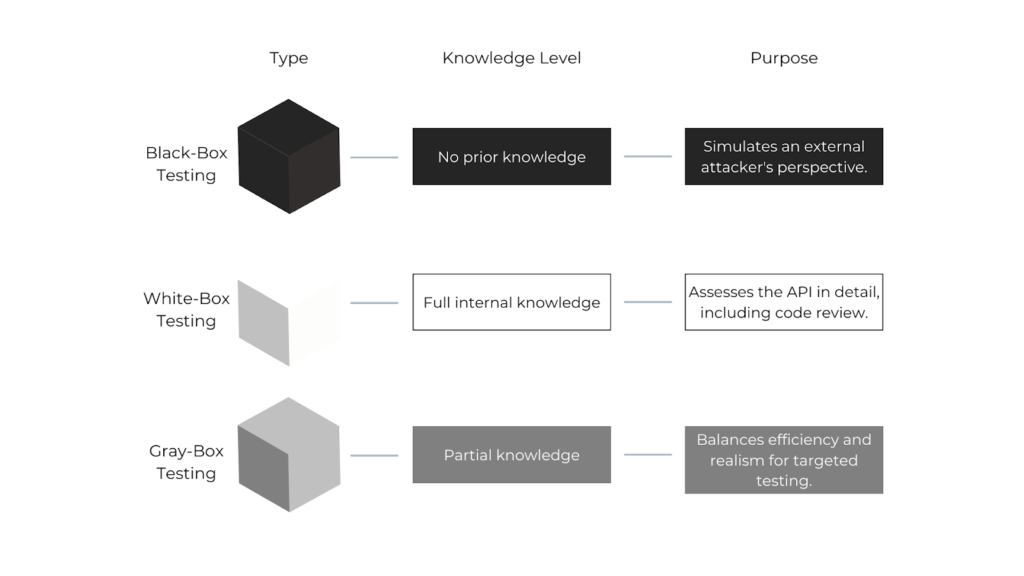
Each method offers unique insights into web application vulnerabilities, helping testers identify weaknesses and fix them before attackers exploit them. For example, black-box testing simulates an external attacker’s perspective, as it requires no prior knowledge of the system. White-box testing, on the other hand, provides full internal knowledge, allowing for a thorough assessment of the API, including code review. Gray-box testing strikes a balance between efficiency and realism by providing partial knowledge, making it suitable for targeted testing.
Key Steps in API Penetration Testing
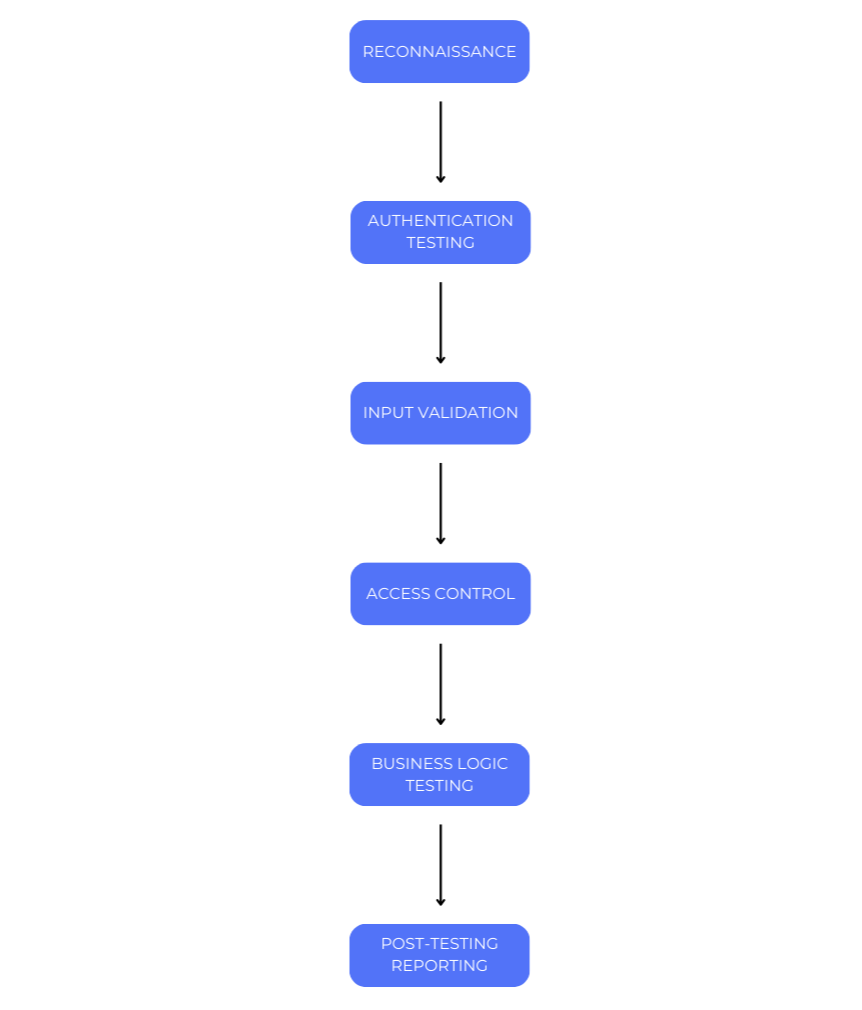
API penetration testing is a comprehensive process that involves several key stages to find and fix vulnerabilities. It begins with reconnaissance, where testers gather API details like endpoints, documentation, and supported protocols. This helps understand the attack surface and identify potential entry points, such as reviewing API documentation, inspecting headers for hidden data, or using tools like Postman or Burp Suite to map out endpoints.
Next is authentication testing, where testers evaluate vulnerabilities in authentication mechanisms. This step looks for issues like weak password policies, improper token handling, or missing multi-factor authentication (MFA). Examples include attempting a brute-force attack to guess passwords or testing whether an expired token can still access endpoints.
Input validation comes next, identifying vulnerabilities in how the API handles user inputs. This step checks for risks like SQL injection, Cross-Site Scripting (XSS), and improper input sanitization. Testers may send malicious inputs like ” OR “1’=’1” to test for SQL injection or <script>alert(“XSS”)</script> to check for XSS vulnerabilities.
Access control is then tested, verifying whether users can access only the resources they’re authorized to. Common issues tested here include Broken Object-Level Authorization (BOLA) and Insecure Direct Object References (IDOR). An example would be modifying a user ID in a request to access another user’s data, like changing /user/123/profile to /user/456/profile.
After that, business logic testing examines whether the API’s workflows can be exploited. Testers look for ways to bypass processes or manipulate system functions. For example, they may try to bypass a payment process by manipulating the API to mark an order as “paid” without actually processing a payment.
Finally, post-testing reporting documents all the vulnerabilities discovered, prioritizing them based on severity. Actionable recommendations for vulnerability mitigation are provided, such as advising on stricter token expiry rules if session tokens are found to be vulnerable to reuse.
This structured approach ensures that potential vulnerabilities are identified and addressed before they can be exploited by attackers.
Common Vulnerabilities Found in APIs
Broken Object-Level Authorization (BOLA):
An object in an application refers to data such as files, user profiles, or records.
BOLA (Broken Object Level Authorization) occurs when an API fails to enforce proper permissions on these objects. Attackers exploit this by altering object references, such as user IDs, to gain unauthorized access to other users’ data.
Example: An attacker sends a request to /user/123/profile and changes the 123 to 124, accessing another user’s profile. Insecure Direct Object References (IDOR) are a type of BOLA vulnerability. These expose sensitive resources by using predictable or guessable object identifiers (e.g., numeric IDs). Without proper checks, attackers can manipulate these references to access restricted data. (If you want to read more about IDOR attacks, you can read our blog here).
Example: An API endpoint like /files/456 allows an attacker to access another user’s file by replacing 456 with the ID of a file belonging to another user, exposing sensitive data.
Excessive Data Exposure:
APIs often return more data than necessary, expecting the client-side application to filter it. This can unintentionally expose sensitive fields, such as passwords or internal configuration details. The risk becomes even more significant when a direct request is intercepted, allowing attackers to view or manipulate the entire response without client-side restrictions.
Example: An API request for user profiles returns not only public details like name and email but also hidden fields such as hashed passwords or admin roles.
Insufficient Logging & Monitoring:
APIs that lack proper logging and monitoring can make it difficult to detect and respond to breaches. Attackers might exploit vulnerabilities over an extended period without being noticed.
Example: A brute force attack on an authentication endpoint goes undetected because no logs are generated for failed login attempts.
Improper Rate Limiting:
APIs without rate-limiting mechanisms are vulnerable to abuse, such as brute force attacks, credential stuffing, or denial-of-service (DoS) attacks.
Example: An attacker floods a login endpoint with thousands of password attempts in a short time, bypassing weak protections.
Weak Authentication Mechanisms:
APIs with not enough authentication make it easy for attackers to bypass security. Common issues include weak password policies, insecure token handling, or lack of multi-factor authentication (MFA).
Example: An API that uses a static API key without additional checks (like IP restrictions or user validation) can be exploited if the key is leaked.
JWT (JSON Web Token) Vulnerabilities:
JWT is widely used for authentication in APIs, allowing users to verify their identity with signed tokens. However, improper implementation can expose APIs to security risks.
Example: Some APIs mistakenly accept JWTs with “none” as the signing algorithm, allowing attackers to forge tokens. If you want to read more about JWT Basics and Security Risks, you can read it here.
CSRF (Cross-Site Request Forgery) Vulnerabilities in APIs:
APIs that do not implement proper anti-CSRF protections can be tricked into executing unauthorized actions on behalf of authenticated users.
Example: A malicious website tricks a logged-in user into making an unintended API request, such as changing account details or transferring funds.
OAuth Related Vulnerabilities:
OAuth is a common authentication framework, but improper implementations can lead to security issues.
Example: A poorly configured OAuth implementation allows an attacker to steal an access token by exploiting open redirect vulnerabilities.
Content-Type Manipulation in APIs:
APIs often process different content types, and improper handling can lead to security flaws.
Example: An attacker sends a Content-Type: application/xml request to an API expecting JSON, leading to XML External Entity (XXE) injection.
Hands-On Practice with Vulnerable API Labs
If you want to practice API security testing in a safe environment, check out these resources:
- https://github.com/riteshs4hu/API-Pentesting-Resources/blob/main/Vulnerable-Labs-Setup.md – This guide provides step-by-step instructions for setting up intentionally vulnerable APIs, allowing you to test real-world security flaws in a controlled environment. It covers various labs designed to help you understand common API vulnerabilities.
- https://github.com/Erdemstar/VulnerableApp4APISecurity – A .NET 7.0-based API designed for hands-on security testing, built around OWASP 2019 API Security Top 10.
- https://tryhackme.com/r/room/bookstoreoc – A Beginner level box with basic web enumeration and REST API Fuzzing.
Practicing with these labs is a great way to improve your skills and get hands-on experience with API penetration testing.
Best Practices for API Security
To minimize risks, consider these actionable steps:
Use secure authentication protocols: Authentication verifies the identity of users or systems, ensuring only authorized access.
- Implement OAuth2 or OpenID Connect for secure and scalable authentication.
- Enforce multi-factor authentication (MFA) to add an extra layer of protection.
- Avoid exposing private API keys in client-side code or storing them in plaintext; instead, use secure vaults or environment variables.
Implement rate limiting: APIs without rate limiting are vulnerable to abuse, such as brute force attacks or denial-of-service (DoS) attacks.
- Limit the number of requests users or systems can make within a specific timeframe (e.g., 100 requests per minute).
- Differentiate rate limits based on user roles (e.g., stricter limits for free-tier users).
- Use API gateways to enforce rate-limiting rules efficiently.
Validate and sanitize all inputs: Unvalidated inputs can lead to injection attacks, which exploit vulnerabilities in APIs.
- Validate input types, formats, and ranges (e.g., ensure a date field contains valid dates).
- Sanitize inputs to remove harmful characters that can be used in SQL injection or cross-site scripting (XSS).
- Use parameterized queries to eliminate SQL injection risks.
Secure communication channels: APIs transmit sensitive data, which can be intercepted if not encrypted.
- Enforce HTTPS for all API endpoints to ensure data encryption during transmission.
- Use TLS (Transport Layer Security) to secure data transfers and prevent man-in-the-middle attacks.
- Regularly update SSL/TLS certificates and avoid using outdated encryption protocols.
Regularly conduct penetration testing: It’s important to run regular penetration tests on your APIs to stay ahead of emerging security threats. Cyberattacks are always evolving, and new vulnerabilities are discovered all the time. By testing your APIs consistently, you can identify weaknesses before attackers do. Here’s how you can approach it effectively:
- Use tools like OWASP ZAP or Burp Suite to detect common vulnerabilities (e.g., SQL injection, XSS, authentication flaws). These tools provide quick insights but should complement manual testing.
- Simulate real-world attacks to uncover complex issues, such as:
Business logic flaws, access control weaknesses (e.g., unauthorized data access), and misconfigurations unique to your API. - Focus on high-risk vulnerabilities like BOLA (Broken Object-Level Authorization), IDOR (Insecure Direct Object References), and improper rate limiting.
- Always conduct penetration testing after updates, integrations with third-party APIs, or new feature deployments.
- Fix vulnerabilities promptly and document the findings to improve your security practices.
- Perform tests more often for critical APIs.
Monitor and log API activity: Monitoring provides visibility into API usage, helping detect and respond to suspicious activities.
- Implement comprehensive logging for all API interactions, including request details, responses, and errors.
- Set up alerts for anomalies like sudden traffic spikes or repeated failed authentication attempts.
- Use centralized logging platforms for efficient analysis and incident response.
- Protect log data to prevent unauthorized access and tampering.
Supply Chain Security: APIs often rely on third-party services and libraries, which can introduce vulnerabilities if not properly secured. Regularly assess the security of external APIs or services integrated with your system to reduce cybersecurity risks from the supply chain. Use vulnerability scanning tools and perform regular security assessments to maintain strong API security. (You can read about a specific case of supply chain security here.)
- Assess the security of external APIs or services integrated with your system.
- Regularly review and update third-party libraries or frameworks to patch known vulnerabilities.
- Evaluate the security practices of vendors supplying APIs or software.
- Use tools like Dependabot or Snyk to track and fix vulnerabilities in dependencies.
- Configure policies to control how third-party APIs interact with your ecosystem, including data validation and rate limiting.
- Maintain a Software Bill of Materials (SBOM), a detailed inventory of all components, libraries, and dependencies within your software. SBOMs help identify vulnerabilities and ensure up-to-date, secure components, improving transparency and risk management.
Additional Tips for API Security:
- Ensure users can only access resources they are authorized to use.
- Implement role-based access control (RBAC) to restrict access based on user roles and permissions.
- Minimize exposure of sensitive data in API responses, such as database IDs or internal server details.
- Encrypt sensitive information both in transit and at rest.
- Use short-lived tokens with expiration policies.
- Ensure tokens are encrypted and securely stored in a key management system.
- Regularly update API software and associated dependencies to patch known vulnerabilities.
- Deprecate old API versions to reduce the attack surface and ensure users migrate to secure versions.
Learning About API Security
If you’re just starting with API penetration testing or want to sharpen your skills, there are plenty of fantastic resources to help you out. Here are some good suggestions to get you going:
- For a comprehensive introduction to API pentesting, check out Practical DevSecOps’ API Security Professional Course. It’s highly recommended for structured and hands-on learning.
- APIsec University offers free training courses focused on API security. They break down common vulnerabilities, show you how to spot them, and provide tips on keeping APIs secure. It’s perfect for beginners and also dives into real-world scenarios.
- If you like exploring things on your own, this GitHub repository is a goldmine. It’s a curated collection of resources like tools, articles, and guides about API security. Whether you’re a beginner or experienced, you’ll find something useful here.
How Laburity Can Help
Laburity specializes in API penetration testing, using the latest API pentesting tools to keep your APIs secure. Our certified experts, with credentials like CEH, EJPT, OSCP, and more, have worked with many clients to improve their API security. Here’s how we help protect your APIs:
- We find vulnerabilities through both automated (using vulnerability scanning tools) and manual testing.
- We make sure your APIs meet the important standards like OWASP API Security Top 10, HIPAA, GDPR, PCI DSS, ISO/IEC 27001, NIST SP 800-53.
- We look for weaknesses in how your API works to prevent logical attacks, ensuring vulnerability prevention.
- We check the security of APIs connected to your system to reduce risks from the supply chain.
- At Laburity, we focus on keeping your APIs safe and preventing security issues.
Conclusion
API security isn’t just about protecting your systems, it’s about building trust, keeping your business running smoothly, and staying ahead of risks. Ignoring API security can lead to serious issues like data breaches, financial losses, and harm to your reputation.
By following cybersecurity best practices like using strong authentication methods, limiting request rates, validating inputs, and securing your supply chain, you can greatly reduce risks. Regularly testing your APIs and monitoring their activity will help you catch and fix problems before they become bigger issues.
At Laburity, we specialize in making APIs safer. Whether you need help finding vulnerabilities, improving security, or staying compliant with standards like OWASP’s API Security Top 10, ISO/IEC 27001, etc. we’re here for you. Our experts use the latest tools and techniques to protect your APIs and your business.
Call to Action
Want to ensure your API is secure? Laburity’s expert penetration testing services can help!
Book a meeting today to get started: https://calendly.com/laburity/meeting.




