Introduction to JWT (JSON Web Token):
JWT, or JSON Web Token, is a fundamental standard outlined in RFC 7519, designed to securely transmit data among parties using JSON objects. Praised for its compactness, readability, and cryptographic signing facilitated by private or public key pairs provided by the Identity Provider (IdP), JWT has emerged as a cornerstone in contemporary authentication methods. Functioning as a token-based, stateless authentication protocol, JWT markedly diminishes server reliance on databases for session management. It plays a pivotal role in modern authentication mechanisms, ensuring the secure exchange of data between parties via JSON objects.
Understanding the Structure of JWT:
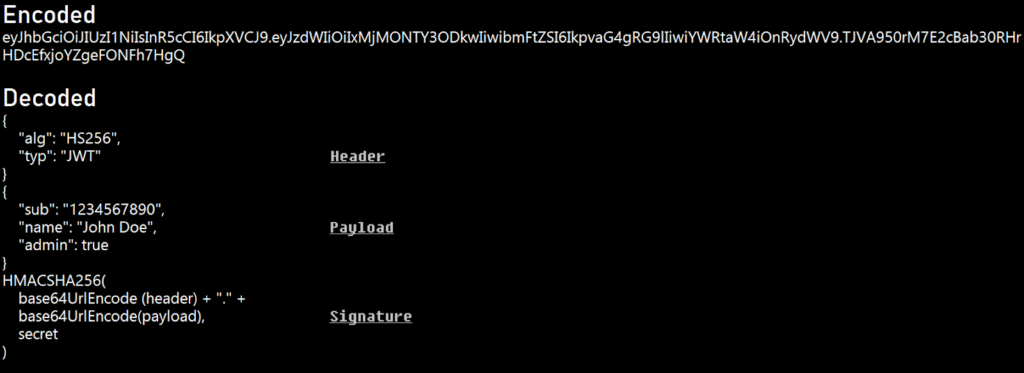
JWT tokens consist of three distinct segments: the header, payload, and signature. Let’s delve into their technical intricacies:
The header segment of a JWT token holds essential metadata, delineating the cryptographic algorithm employed for encoding and the type of token being utilized. For instance, a typical JWT header might appear as follows:
{
“alg”: “HS256”,
“typ”: “JWT”
}
In this example, “alg” denotes the algorithm used for encoding, with “HS256” indicating HMAC with SHA-256. The “typ” field specifies the token type as JWT (JSON Web Token). This concise metadata within the header serves as a blueprint for verifying and processing the token’s contents, facilitating secure authentication and data exchange across digital environments.
The payload segment of a JWT token encapsulates crucial user data, exemplified by attributes like the subject (sub), name, and admin privileges. For instance, a JWT payload might resemble the following JSON structure:
{
“sub”: “1234567890”,
“name”: “John Doe”,
“admin”: true
}
Here, “sub” represents the user’s unique identifier, “name” signifies their name, and the “admin” attribute denotes their administrative privileges. This structured payload facilitates seamless authentication and authorization processes, enabling systems to accurately verify user identities and enforce access control policies based on their roles and permissions.
The signature segment of a JWT token plays a pivotal role in ensuring the token’s integrity and authenticity through cryptographic validation. This validation process typically involves using an algorithm such as HMACSHA256 to generate a signature based on the concatenated base64UrlEncoded header and payload segments, along with a secret key. For example, the signature calculation can be represented as:
HMACSHA256(
base64UrlEncode(header) + “.” +
base64UrlEncode(payload),
secret)
This cryptographic operation generates a unique signature that serves as a tamper-evident seal for the JWT token. By verifying this signature against the token’s contents and the secret key, recipients can authenticate the token and confirm that it has not been altered or manipulated since its creation. Thus, the signature segment safeguards the integrity and trustworthiness of JWT tokens in digital communication channels.
Exploring JWT Token Vulnerabilities:
Information Leakage:
The absence of encryption in JWT tokens exposes them to information leakage, potentially compromising user privacy when decoded. Attackers can intercept and decode JWT tokens, gaining access to sensitive user data stored within the payload. This includes personally identifiable information (PII), authentication credentials, and session tokens. Without proper encryption measures, such as JSON Web Encryption (JWE), organizations risk exposing critical data to unauthorized parties, leading to privacy violations, identity theft, and fraud. Therefore, implementing encryption techniques is essential to safeguarding the confidentiality and integrity of JWT tokens and mitigating the risk of information leakage.
Injection of New Public Key in Token Header:
The injection of a new public key within the token’s header involves an attacker clandestinely embedding a new key within the header, manipulating the token’s verification process. Consequently, the server unwittingly employs this rogue key to validate the token’s signature, leading to potential security breaches (CVE-2018-0114). This exploit can be executed utilizing tools such as the “JSON Web Tokens” Burp extension, which streamlines the process of injecting the malicious key into the token’s header. By sending the manipulated request to the Repeater and selecting the “CVE-2018-0114” option within the JSON Web Token tab, attackers can trigger the vulnerability, potentially compromising the integrity of the authentication mechanism.

None Algorithm Attack:
JWT’s support for the “none” algorithm introduces a vulnerability, allowing tokens with empty signature sections to be validated if the algorithm field is set to “none”. This flaw can be exploited by various bypass attempts, including ‘nOne’, ‘NONE’, and ‘NonE’.
{
“alg”: “none”
}
KID Parameter Attack:
Exploiting the Key ID (KID) parameter within JWT tokens can lead to security breaches, such as command injection and SQL injection, if not rigorously validated. Attackers may manipulate the KID parameter to bypass authentication mechanisms and execute malicious commands, posing a serious risk to the integrity of the authentication process.
Changing the Algorithm:
Manipulating the algorithm from “RS256” to “HS256” alters the encryption workflow, transitioning from asymmetric to symmetric encryption.
{
“alg”: “HS256”
}
JSON Web Key (JWK) Vulnerabilities
Additionally, it’s crucial to address vulnerabilities related to JSON Web Key (JWK) usage in JWT tokens. Attackers may exploit weaknesses in the JWK implementation, leading to security breaches and unauthorized access. Let’s delve deeper into JWK vulnerabilities:
JSON Web Key (JWK) is a JSON data structure used to represent cryptographic keys, often used in JWT tokens for signature verification and encryption. However, vulnerabilities can arise if proper precautions are not taken in handling and validating JWKs.
Consider the following JWK object:
{
“alg”: “RS256”,
“jwk”: {
“kty”: “RSA”,
“n”: “1cNygNJEKlIR5lKaI8d7YK3AtiNSdhQXy2nVsxLGqMzfPmLYuH4Fvl8O8URzwz5mmchJESlnGrWJyp1D7Yhc3mwkC7muRaoWmMTub4G0FLasfVrgDbHNNEMj58cInhHlSyN6MygsNzFA5mXlPK–BMDjM-34ENZlpg0GGlZDShFDF0GXllblp3Vz9MGFpC8G8jPOi9GlO5TOL1sIXklFtzYOpgXDFyU8mXc4RF4w37aT1Zq-YBEXtQe-2aLjZtx6OyDCDdBHt-pwB4JhJPC6JmnQI9pXc3aJlGItiR6cDn6MIMVy1aNTk09vOaSLGMLuubzdXY8qntoDaL3bzL7b9Q”,
“e”: “AQAB”,
“use”: “sig”
}
}
This JWK object specifies an RSA key with the “RS256” algorithm. The “n” (modulus) and “e” (exponent) parameters represent the key’s components, while the “use” parameter indicates the key’s intended usage, in this case, for signature verification. Attackers may exploit vulnerabilities in the JWK object’s parameters to manipulate the key’s behavior and circumvent authentication mechanisms. For instance, they might tamper with the “alg” parameter to change the cryptographic algorithm used for signature verification or encryption. Additionally, attackers could modify the “n” (modulus) and “e” (exponent) parameters to weaken the key’s strength or impersonate legitimate users.
Impact of JWT Token Vulnerabilities:
Sensitive Information Disclosure:
Vulnerabilities in JWT tokens can result in the disclosure of sensitive information, including user credentials, session tokens, and personal data, leading to identity theft, fraud, and privacy violations.
Compromised Client Authenticity:
Attackers can manipulate JWT tokens to impersonate legitimate clients, bypassing authentication mechanisms and gaining unauthorized access to protected resources, compromising the integrity and trustworthiness of client-server interactions.
Account Takeover:
Exploiting vulnerabilities in JWT tokens can facilitate account takeover attacks, allowing adversaries to hijack user sessions, escalate privileges, and perform malicious actions on behalf of legitimate users, jeopardizing the security and confidentiality of user accounts.
Unauthorized Access to Server Files:
Weaknesses in JWT token validation can enable attackers to gain unauthorized access to server files and resources, potentially exposing sensitive data, proprietary information, and intellectual property to unauthorized parties.
Potential Extraction of Data from SQL Databases:
Security flaws in JWT tokens can be leveraged to execute SQL injection attacks, enabling attackers to extract sensitive data from backend SQL databases, manipulate database queries, and compromise data confidentiality, integrity, and availability.
Conclusion:
Understanding JWT token vulnerabilities is vital for keeping authentication systems safe. With the right knowledge and examples, security experts can find and fix problems, making sure digital environments stay secure. But it’s not just about knowing stuff – staying alert and working together are also important. Regular checks and sharing knowledge help teams stay ahead of threats. By doing this, organizations can keep their systems safe and trusted by users.




