In the ever-evolving landscape of cybersecurity, uncovering vulnerabilities is crucial to maintaining the integrity and security of digital platforms. In this write-up, we explore a recently discovered flaw in the access control system, shedding light on the potential risks and impacts it poses.
The Discovery:
Our journey begins with the identification of an improper access control issue on one of our clients. This vulnerability allows a teacher user to extract sensitive information from the administrative dashboard. The compromised data includes PII that is usernames, complete names, emails, and unrestricted access to the administrative interface.
Understanding the Risk:
The real danger lies in the potential exploitation of this vulnerability. An attacker could gain unauthorized access to the administrative dashboard, providing them with a comprehensive view of the organization’s administrators. This opens the door to a wealth of sensitive information that could be misused if it falls into the wrong hands.
Our Approach:
Our journey kicks off with the adoption of a teacher persona, armed with provided credentials for access. The mission is clear: to investigate the system’s security and integrity. Here’s how the
Journey unfolded:The initial step involves leveraging the provided credentials to gain entry into the system. Armed with the username and the associated password of the role teacher user, we log in to the platform.
- Navigating the Terrain
- Once within the system, the focus shifts to the logged-in user’s profile. Navigating to the user’s profile URL https://redacted.com/accounts/1/external_tools/198 is the natural progression in understanding the system’s structure and permissions.
2.. Unsuccessful Probing
- Attempting to access the admin’s account URL, a roadblock is encountered. An error message, indicating an apparent restriction was appeared. This is a pivotal moment in the journey, highlighting the initial layers of defence.
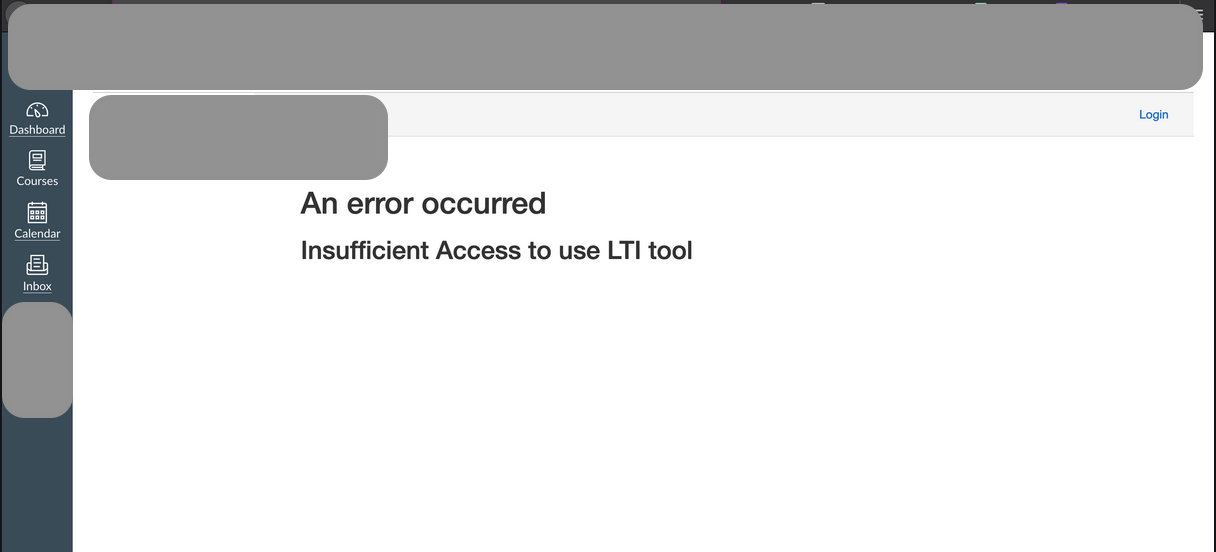
3.. Unraveling the Vulnerability
However, the story doesn’t end there. Recognizing the potential vulnerability in the system’s architecture, our exploration takes a turn towards URL manipulation. By skillfully manipulating the URL as https://redacted.com/accounts/1/external_tools/4?launch_type=global_navigation , the teacher user finds a gateway to the administrative portal.
The key points that we noticed during the audit was the ID 4 and the parameter lauch_type with value global navigation. Using these values the administrative portal was exposed to teachers portal.

4.. The Unintended Revelation
Astonishingly, alongside an error message, the dashboard unveils sensitive information – emails and other details belonging to the administrators.
Conclusion:
This discovery underscores the critical importance of robust access control mechanisms. Organizations must promptly address and rectify such vulnerabilities to safeguard their systems and user data.
Closing Thoughts:
As technology advances, so do the methods of those seeking to exploit its weaknesses. It is our collective responsibility to stay vigilant, continuously assess our digital defences, and address vulnerabilities promptly to ensure a secure online landscape for everyone.




